Atholee Shearer's
Seminar Portfolio

Mini Event Reflections
Three Things I Learnt
✽ Research Committee
- Everyone has a personal brand. It communicates values, strengths, and passions both online and in person. Being intentional about it through appearance, communication, and social media can help to make me stand out in the competitive professional world
- Networking isn’t about collecting as many contacts as possible. It is about fostering a meaningful relationship with people who align with my goals and values.
- Consistently sharing my work, interests, and insights can build my visibility and credibility. Also, I should try to curate my digital footprint to reflect my professionalism.
✽ Accounting Committee
- The main goal of the Insolvency Act is based on rehabilitation, not punishment. It is designed for the “honest but unfortunate debtor” who deserves a fresh start rather than retribution.
- There are four procedures available for dealing with insolvency, namely Information Proposals, Receivership, Proposals, and Bankruptcy. Each has specific criteria and steps that ensure the process is fair and transparent.
- Creditors can amend or reject a debtor’s proposal, and they can also apply to the court to lift a stay or ensure that payments are made. These rights help to balance the interests of both debtors and creditors.
✽ Marketing Committee
- Building a healthy lifestyle takes a lot of effort, like fostering a balanced nutrition, regular exercise, and sufficient sleep. I realised that I was falling behind on many of the recommendations the presenter made, such as spending at least 30 minutes on moderate-intensity activities five days a week, maintaining a sleep schedule, and staying hydrated.
- Strategies like managing stress through having hobbies, journaling, limiting social media, and building strong social support systems are key to my emotional well-being.
- I learnt that budgeting, learning about investing, and setting work-life boundaries are critical to my wellness beyond university.
Conference Day Reflections
René Roper | Fireside Chat
René Roper had a highly informative discussion with the MC during the Fireside Chat session that focused on the realities and risks surrounding data breaches in organisations, many of which I had no prior knowledge of. She offered a direct look into the common dangers businesses experience when it comes to data security. She emphasised that it is alarmingly easy for data breaches to occur. It can happen due to of weak passwords, mishandling confidential files or the unauthorised sharing of information. One of what I believe to be the most impactful parts of her discussion was her dissection of ‘role-based access control’, which ensures that employees only have access to the data necessary for their specific roles. She gave the example of a low-level employee in the HR department having access to information about the salaries of the company’s executives. She stressed the significance of having this practice as a preventative measure to reduce the company’s vulnerability to data breaches.
Roper also spoke about compromised and malicious employees, bringing attention to the internal threats businesses face. Sometimes, external hackers are not the only cause of data breaches; rather, they are employees who have been compromised either unintentionally through phishing attacks or intentionally for malicious gain. She highlighted that even carelessness can put a company at risk and give access to sensitive data. An example was given of a department having access to sensitive information via a shared password that wasn’t changed when an employee left the company. This type of carelessness leaves a company vulnerable to data breaches and These types of breaches can cause damage beyond financial loss; they can lead to a spoiled reputation and a loss of public trust.
What I knew before:
• I had previous knowledge of Jamaica’s Data Protection Act prior to conference day from other modules.
• I also had a basic knowledge of hacking and cybersecurity threats.
What I learnt:
• Jamaica’s Data Protection Act is unique in including criminal penalties, not just financial ones, which surprised me because I assumed that all data protection acts carried criminal punishment.
• Businesses hire ethical hackers to help them identify any vulnerabilities and prevent data breaches.
Khiana Chutkhan | Securing the Future: Data Protection and Cybersecurity in Human Resource Management
Mrs. Khiana Chutkhan’s presentation provided valuable insights into the role of the Major Organised Crime and Anti-Corruption Agency (MOCA) in data protection within Jamaica. She gave a bit of a background on MOCA’s operations and its collaborative role with organisations to ensure data is safeguarded against misuse and abuse. A significant part of her presentation involved explaining how MOCA supports investigations into data breaches and enforces accountability when breaches occur. She also delved into the importance of background checks, particularly during recruitment, emphasising how this process is key to filtering out individuals who may pose a data security risk. It was also interesting to learn how HR departments may have a bigger role in data protection than IT departments.
Mrs. Chutkhan pointed out that HR professionals are on the frontlines of data security since they handle large volumes of personal and sensitive employee data and are often the main targets of data breaches. HR’s role includes being vigilant against phishing emails and scams, especially the ones designed to steal employee or organisational information. She gave some advice on how to identify phishing attacks and encouraged everyone to develop stronger habits around protecting their own personal data. At the end of her presentation, Mrs. Chutkhan implored us to understand that data protection isn’t just a task for IT but a shared responsibility that involves every department and every employee.
What I knew before:
• I was aware that Human Resource departments handle employee data.
• The importance of creating strong passwords
What I learnt:
• Tips and tricks on identifying and avoiding phishing attacks, like typing in URLs myself instead of clicking a suspicious link.
• Daily practices for protecting personal data, including limiting access and proper data disposal.
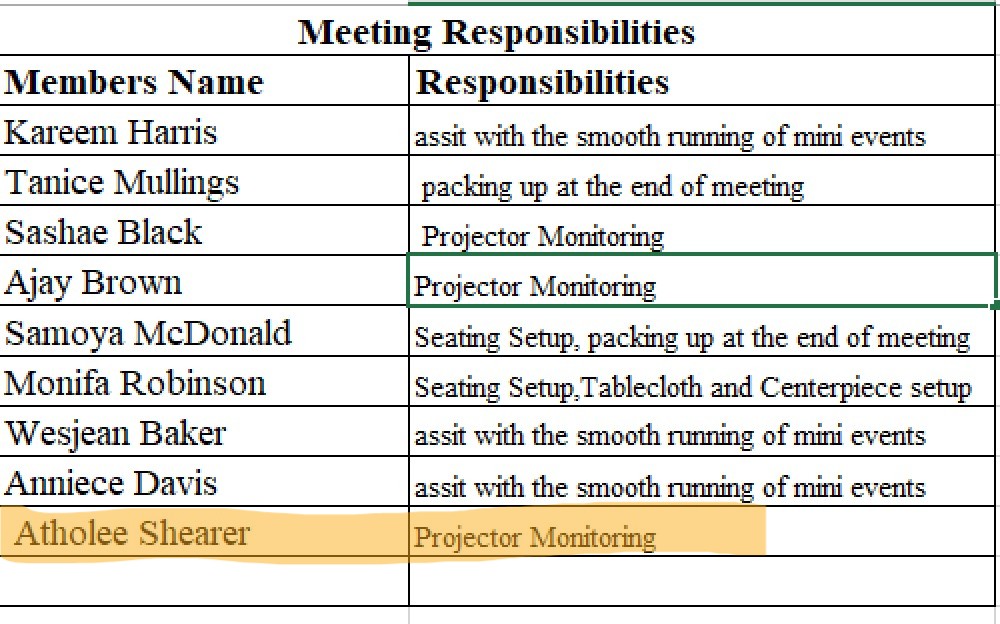
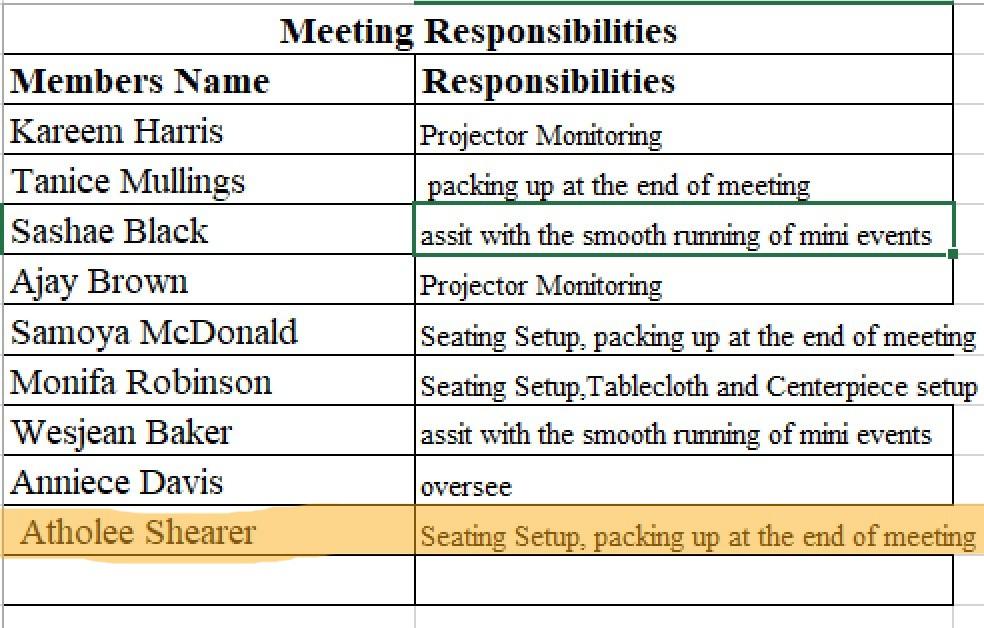
Committee Contributions
Throughout semester two, my role as a member of the Logistics Committee consisted of ensuring that the classroom was set up for weekly seminar meetings and occasionally monitoring the projector as well as packing up at the end of the meeting. I assisted in the creation and presentation of our attempt at making a seminar pledge and assisted with facilitating the debate activity of our mini-event.
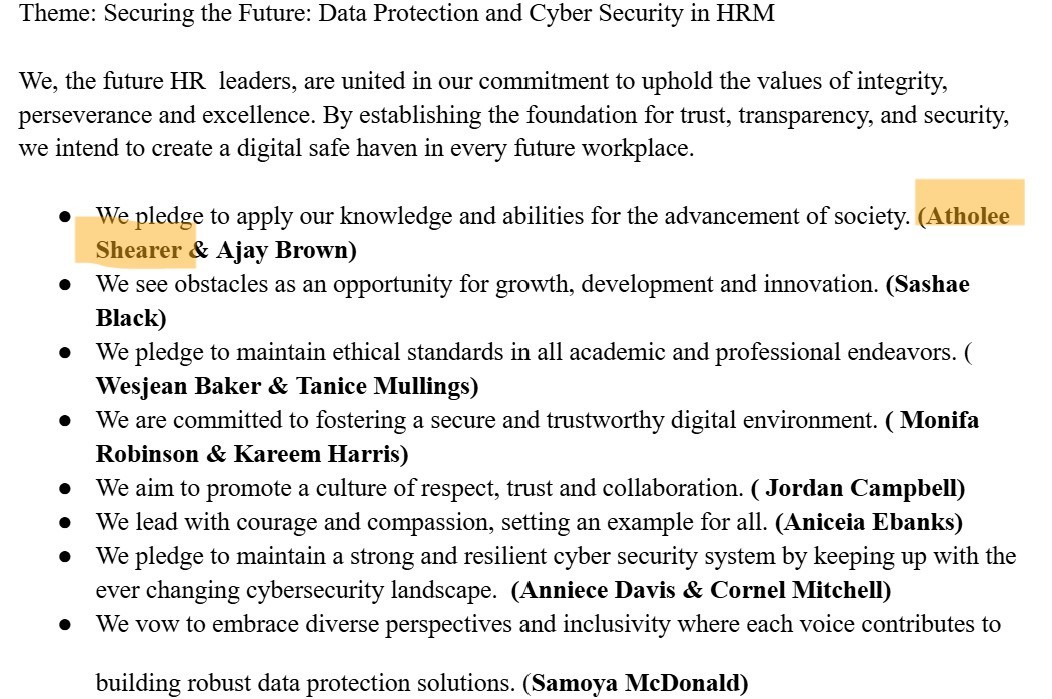
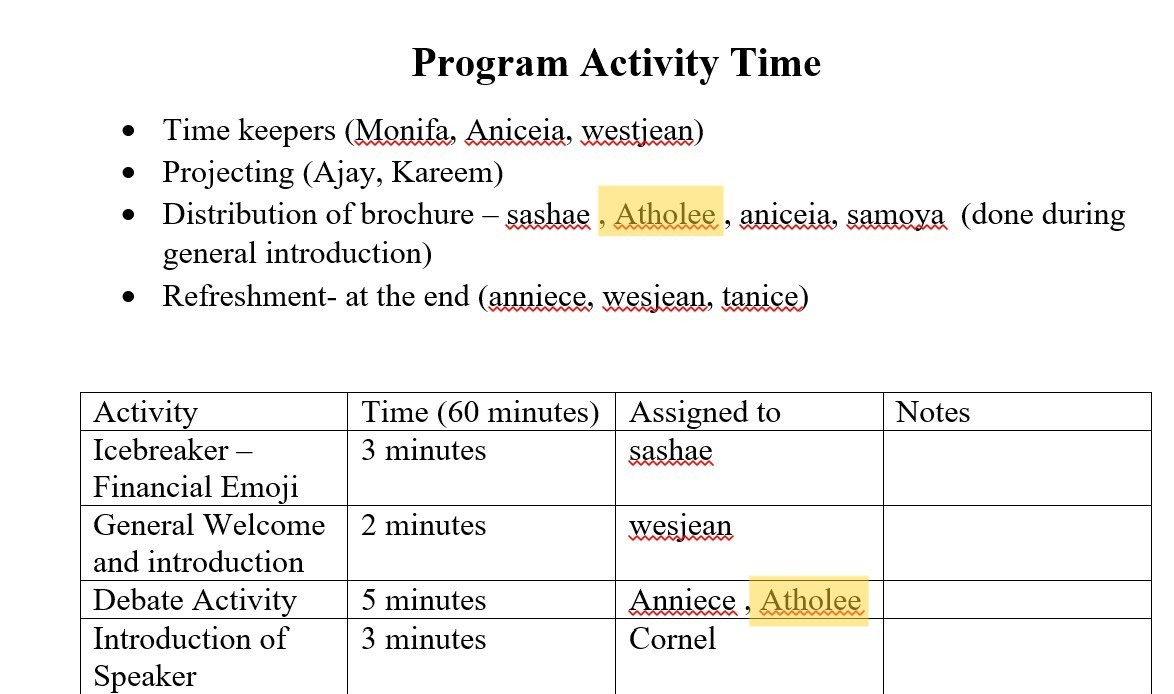

Seminar Activities Support



iCandy Support at Marketing Seminar's Flirt
iCandy Support at the 420 Lounge
Charity Event
Conference Day