SASHAE BLACK'S
SEMINAR PORTFOLIO

THREE THINGS I LEARNT FROM THREE MINI EVENTS
Secretariat Mini Event
1.The speaker discussed three factors that influence employee engagement, these include; leadership, work environment and career development
2. Different types of employee appreciation include; verbal/written, incentives and rewards as well as career development opportunities
3. Strategies for embedding appreciation in the workplace includes but not limited to; recognition, training and development and open communication.
Accounting Mini Event
1. The meaning of insolvency, which is when a person or company is completely incapable of paying off its financial obligation.
2. Also that The Insolvency Act 1986 covers the process by which individuals or companies can declare bankruptcy.
3. According the Insolvency Act, 2014 after being declared bankrupt all the property of the insolvent person vest in the trustee of the insolvent person’s estate.
Professionalism Mini Event
- The speaker looked at the common types of mental illness such as: Anxiety disorders, depression Bipolar Disorder and Schizophrenia etc .
- The speaker emphasized that the stigma against mental health in Jamaica is still there and it often ends up blocking people seeking help, especially men.
- The speaker also stated that females tend to attempt suicide, whereas males tend to commit it.
Summary of two presentations made on Conference Day
✽ Speaker: Senior Special Agent Khiana Chutkhan
Securing the Future: Data Protection and Cybersecurity in Human Resource Management
-
The presentation looked at phishing and ransomware attacks, stressing the need and emphasis on cybersecurity awareness. Phishing attacks involve sending a deceptive message to an individual, usually an email or text, to trick the user into yielding sensitive information, usually username and passwords. These messages act like legitimate platforms and are aimed to look authentic to an eyesore. As soon as a user types in or submits their information, the attacker copies it and tries to apply it in other applications. Attention could be drawn by the speaker towards the various indicators a user should check for: spelling errors, strange URL, or in some cases unusual information about sender identity. Users should type in web addresses into their browsers instead of clicking any embedded link.
Two things I knew before:
- Phishing attacks typically arrive in the form of emails or texts that pretend to fit customer platforms, tricking people into giving sensitive information like a username and password.
- Also, that one way of staying safe is to refrain from clicking on suspicious message links and type the actual address in the browser.
Two Key Takeaways:
- Always double-check whether an email or text may be genuine by making sure there are no spelling errors or suspicious URLs from unknown senders.
- Both individuals and organizations face a major threat from a ransomware attack. Do not pay the ransom; it is only an assurance that your data will not be restored, and it only encourages future attacks.
✽ Speaker: Rene Roper
The speaker pointed out three varieties of risky employee behavior for cybersecurity considerations: compromise, negligence, and criminality. A compromised employee might unwittingly impose threats by means of an infected flash drive, for instance. Between mistakes like responding to confidential mails and careless disclosure of attachments from which salary information might be derived, a careless employee can incite internal conflicts and data leakage. The discussion illustrates that access should be controlled on the basis of roles given to prevent unauthorized viewing of sensitive information.
Two things I knew before:
- That employees can pose a cybersecurity risk, be it intentionally or unintentionally, due to negligence or ignorance.
- I was also aware of an internal conflict resulting from careless disclosure of confidential information such as salaries.
Two takeaways:
- Even the simplest of errors, such as using an infected device or misdirected emails, can result in serious security breaches.
- Role-based access control can help restrict access to sensitive data and therefore mitigate the risk of internal data leakage.
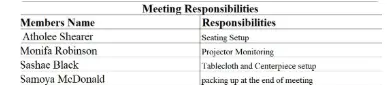
Significant Contributions made to my committee in Seminar 2
Pictures participating in/supporting Seminar 2 activities

Conference Day

Charity Event
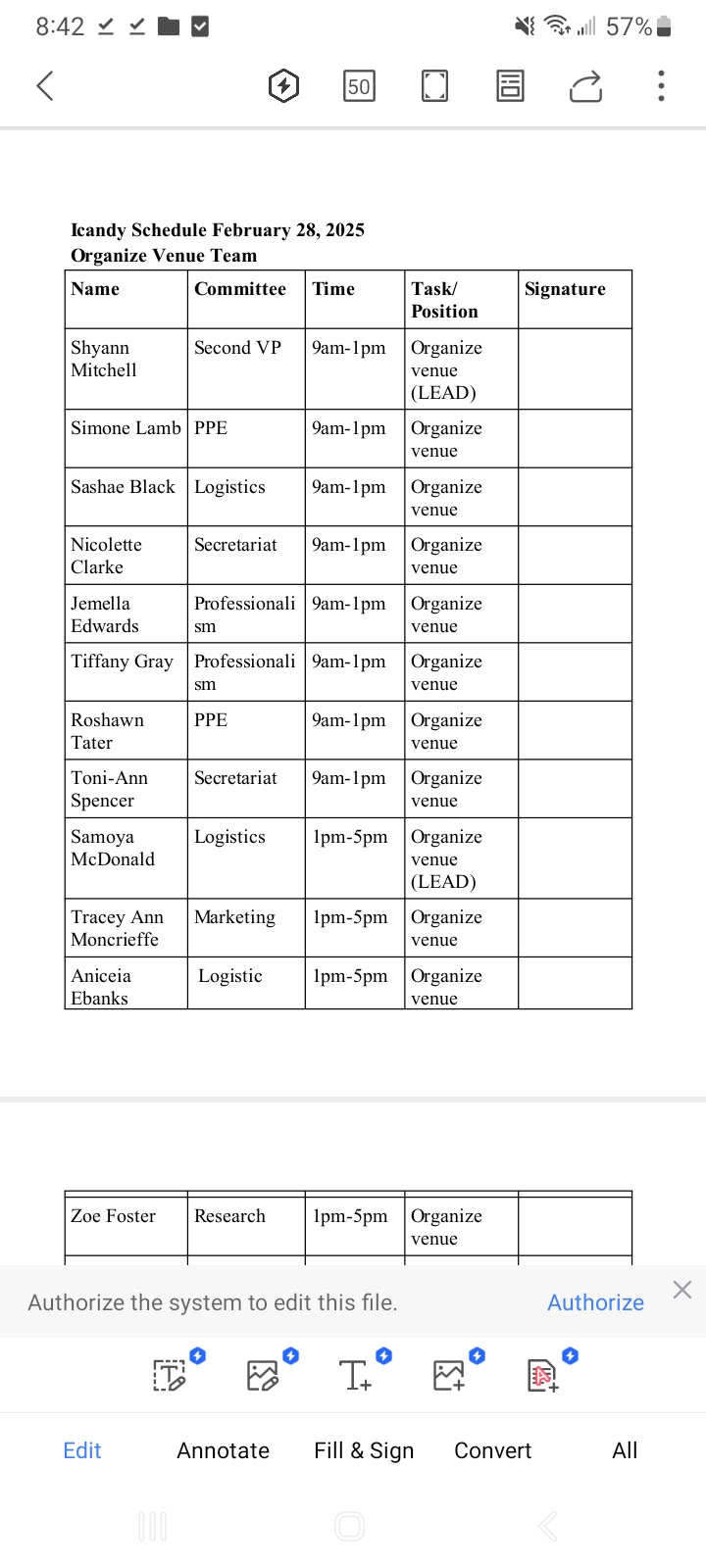
Icandy
I assisted with the organization of the venue because I had stated that I would be unable to attend the event.